In the last two weeks, we have talked about digital estate plans and why it is crucial for businesses today to have one. Since most business data is now stored digitally, it makes sense to protect these
1600 Mill Rock Way, Bakersfield, CA 93311 (661) 281-4000 sales@arrc.com
- Home
- Uncategorized
Cybersecurity insurance protects businesses in the event of online attacks. Insurance providers can absorb a considerable amount of the impact, allowing companies to recover faster and get back on track after experiencing a cyber breach. Recent data
When starting a business, it is only natural for the business owner to dream of success and business growth for their new venture. But having a dream is not enough. There also needs to be a strategic
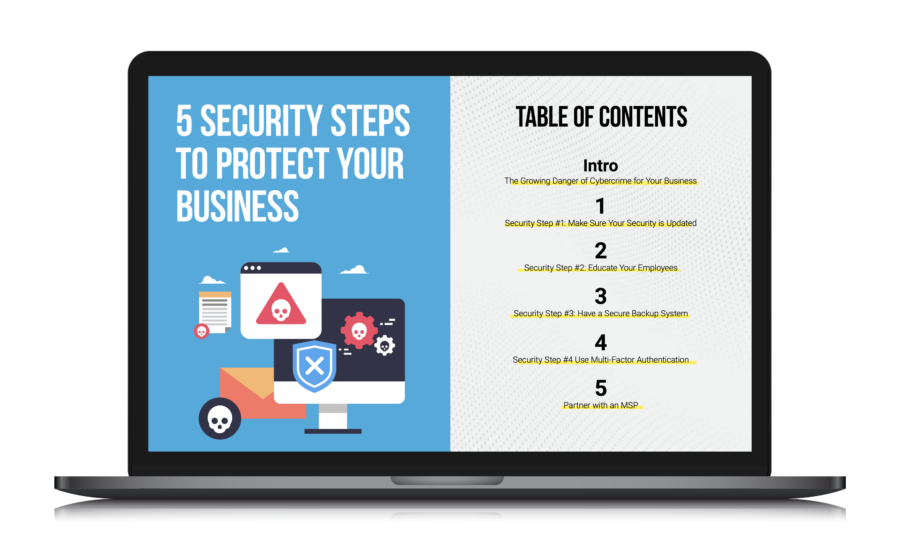
Cybercrime is a growing threat It’s not buzz, and it’s not sensationalism. The growing awareness of cybercrime is long overdue and is frankly just beginning. We want to give you an e-book 5 steps to protect your
Keeping your business network safe and secure is essential. Virtual offices and cloud services can be smart ways to keep your data safe. However, many people do not understand the benefits that investing in virtual offices can
Artificial intelligence, also referred to by the simpler term AI, has long been the holy grail of futurists, science fiction authors, and fantasists alike. Even before we established the concept of computer science, the notion of mechanized entities capable
If your business is at the point where you're thinking about hiring a fulltime IT tech, congratulations! Having enough consistent needs to fill this role means you’ve worked hard and made good decisions that drove business growth.
With the ongoing situation in the world, there are many people who are furloughed or laid off from their jobs. Those of us who can work from home are very fortunate to be able to keep working
Just as people were starting to get in front of stay-at-home recommendations with robust video conferencing and on-line learning options, “zoombombing” was born, proving yet again that evil knows no bounds. Zoombombing occurs when hackers break into